It’s no secret I like Virtualization technologies a lot. I have written several other articles on some of my tips and tricks mostly involving creating Virtual Machines of OS X. You can read some of those here, here, here or simply just search my blog.
For those who support multiple operating systems or simply have a desire to learn about them, Virtualization is a fantastic way to just that. Virtualization, in computing, is the creation of a virtual (rather than actual) version of something, such as a hardware platform, operating system, a storage device or network resources. Here is a good description tailored to the IT professional or CEO http://youtu.be/MnNX13yBzAU but you can get a good grasp of the concepts.
At my organization I have installed and manage a VMware ESXi clustered installation on a SAN (Storage Area Network) with hardware and software that starts in the six figures. This is obviously way out of reach of the home user or enthusiast. But Virtualization can be inexpensive and or downright free for the taking. Microsoft, VMware and Virtual Box all have freeware solutions!
For this article I am going to concentrate on the hardware required and the simplest to use application for the novice or even intermediate user – VirtualBox a freeware application by Oracle. So on to the hardware:
Virtualization product or solution such as VMWare Workstation (and the ‘industrial ESXi), VirtualBox and Windows Virtual PC often require Hardware Assisted Virtualization (HAV) CPU feature in order to function properly as it allows a virtual machine hypervisor to run an unmodified operating system without incurring significant emulation performance penalties. The largest chip makers, Intel and AMD implement hardware assisted virtualization in their processors as Intel VT (VT-x) and AMD-V respectively. However, not all modern CPU has hardware-assisted virtualization capability built-in though; you will want to make sure. The VT capability in the processor on the computer is built onto the tiny piece of chip, and cannot be added or removed using any manual process. And even if the CPU features VT, it must be enabled in BIOS.
Most newer CPUs include VT operation by default. However, some older or even current processors available for purchase for DIY or operating on OEM computers may not support VT. When there is no VT support, Virtual Machine Technologies based on VT may fail to install or cannot be powered up and started.
If you are going to create or use virtual machines you should verify, check, determine or get to know whether his or her PC computer supports hardware-assisted virtualization. There are a few software utilities you can use to quickly determine whether there is hardware virtualization system on the system CPU. One is name named SecurAble which is able to display hardware virtualization support status as Yes, No, Locked On and Locked Off. The other is Microsoft’s HAV Detection tool.
SecurAble Detects CPU Processor Security Features (Bit Length, DEP and Virtualization)
Most users who buy computer are just paying notice to the speed (how fast) and size of RAM memory (how big) of the PC. In fact, most modern CPU microprocessors have great lots of features and capabilities other than constantly higher clock rate. With the evolving of software development, some of these features are now required. With SecurAble, user can easily check and determine if the system is x86 or x64 architecture, support hardware DEP and/or hardware virtualization.
SecurAble probes the system’s processor, determine the presence, absence and operational status and displays the status of the three most significant security-related processor features:
- 64-bit instruction extensions
- Hardware support for detecting and preventing the execution of code in program data areas
- Hardware support for system resource “virtualization”
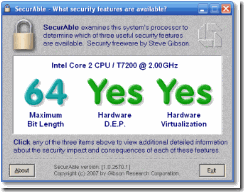
All these features are deemed to be security-important by developer of SecurAble, GRC. 64-bit capable CPUs have the ability to run the 64-bit versions of Microsoft’s substantially more secure Windows XP, Windows Server 2003, Windows Vista, Windows Server 2008 and Windows 7 operating systems, which has the operating system kernel locked down. Hardware-enforced DEP can stop exploitation of buffer overflow attacks, while virtualization technology (VT) can be used to create fully contained environments that can be used to insulate the real hosting operating system from any actions taken by software running within the “virtual” environment.
SecurAble is free to use, and no installation require.
I use SecurAble the most for checking for Hardware-Assisted Virtualization.
Download SecurAble.
http://www.grc.com/securable.htm
Microsoft has also released a application tool that able to detect status of Hardware-Assisted Virtualization (HAV) support on the computer system’s CPU microprocessor. Aptly named as Hardware-Assisted Virtualization Detection Tool or simply as HAV Detection Tool, the utility can detect and check if the computer meets the processor requirements to run Windows Virtual PC, i.e. hardware-assisted virtualization.
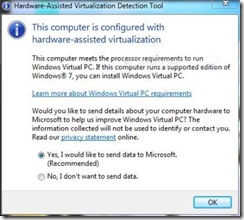
Download HAV Detection Tool: havdetectiontool.exe
Using HAV Detection Tool is easy, just run the executable, and the results of whether hardware virtualization support is existed on the system or not (together with ability to install Windows Virtual PC) will be displayed on result dialog. It’s standalone program, thus no installation or un-installation required
So after you’ve determined you can run virtual machines with HAV you’ll want to try some VM’s out.
As I mentioned for home use I’ve found Virtual Box to be the easiest to use and configure. You can get it here and get the ‘Extension Pack’ here. Install the application first (get the right one for you platform – Windows, Mac, Linux) Then install the Extension pack; it will install automatically IF you’ve already installed the base application first.
Once installed you are ready to start working with just about any operating system you want to within your current system!
Here is a fantastic walk through of how to simply create a VM from a downloaded Linux installation disk (ISO)
This method can be used for installing Windows VMs too! If you have a Windows installation CD/DVD and you wish to install it as a VM you can. [For OS X you will have to follow some of the very specific tutorials I have put together – Apple does not like you to install OS X on non Apple hardware]
VirtualBox.org has a very detailed description and walkthroughs too, you can find that here.
The easiest way to get started with VirtualBox is to import an already made image/appliance. Virtualbox.org has many already made Linux installations you can get them here. And with a little diligent searching you can find LOADS of them.
I hope this helps some to get started and have a better understanding of these technologies. More knowledge and experience can only be good.
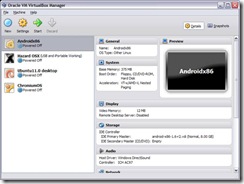
Here is an image of some of the VM’s on one of my home machines in Virtual box.
As I noted if you are interested in OS X VMs you can go here and read the second half on using Virtual Box. Here are two walkthroughs from other tech sites worth checking out too.
http://thetechjournal.com/electronics/computer/steps-to-install-mac-os-x-snow-leopard-in-virtualbox-on-windows-7.xhtml
and here: http://www.sysprobs.com/mac-os-guest-virtualbox-326-snow-leopard-1064-windows-7-32-bit



