Okay folks, here we go again. More ransomware is spreading and it can hit you. [Ransomware comprises a class of malware which restricts access to the computer system that it infects, and demands a ransom paid to the creator of the malware in order for the restriction to be removed. Some forms of ransomware encrypt files on the system’s hard drive (cryptoviral extortion), while some may simply lock the system and display messages intended to coax the user into paying.]
Ransomware/Malware that encrypts your data and tries to sell it back to you, or else, is not new. In fact, one of the earliest pieces of malware that was written specifically to make money, rather than simply to prove a point, was the AIDS Information Trojan of 1989. That Trojan scrambled your hard disk after 90 days, and instructed you to send $378 to an accommodation address in Panama.
Enter the latest Menace – CryptoLocker. If you have become seriously infected and do not take IMMEDIATE remedial steps, there is, sadly, not much you can do [unless you have full ‘offline’ backups as I am always ranting about] but pay up!
This is getting some recent much needed attention by the press. Here is a recent short article. A Google search will turn up hundreds more.
The endgame is the same in all cases: if you have a reliable and recent backup, you’ll have a good chance of recovering without too much trouble.
Prevention, in this case, is significantly better than cure:
- Stay patched. Keep your operating system and software up to date.
- Make sure your anti-virus is active and up to date.
- Avoid opening attachments you weren’t expecting, or from people you don’t know well.
- Make regular backups, and store them somewhere safe, preferably offline.
Don’t forget that services that automatically synchronise your data changes with other servers, for example in the cloud, don’t count as backup!!
They may be extremely useful, but they tend to propagate errors rather than to defend against them.
What is CryptoLocker
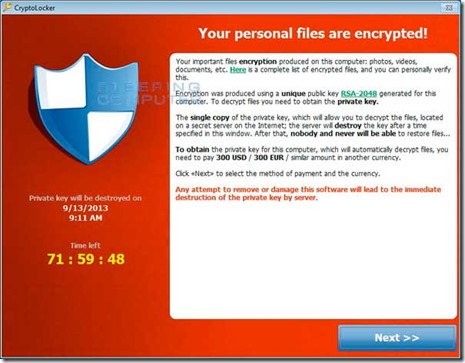
CryptoLocker is a ransomware program that was released around the beginning of September 2013 that targets all versions of Windows including Windows XP, Windows Vista, Windows 7, and Windows 8. This ransomware will encrypt certain files using a mixture of RSA & AES encryption. When it has finished encrypting your files, it will display a CryptoLocker payment program that prompts you to send a ransom of either $100 or $300 in order to decrypt the files. This screen will also display a timer stating that you have 72 hours, or 4 days, to pay the ransom or it will delete your encryption key and you will not have any way to decrypt your files. This ransom must be paid using MoneyPak vouchers or Bitcoins. Once you send the payment and it is verified, the program will decrypt the files that it encrypted.
How do you become infected with CryptoLocker
This infection is typically spread through emails sent to company email addresses that pretend to be customer support related issues from Fedex, UPS, DHS, etc. An unsuspecting computer user will either get an email purporting to be from their bank, friends, Facebook or a host of other fake senders or be asked to click on a pop up in a Website. The person thinks it’s legitimate, clicks on it and before they know it the virus is installed on their computer which encrypts their data. The person will be given a time period, for instance 72 hours, to make a payment in exchange for the key to decrypt all the data. Refuse and the data on the hard drive will be gone forever.
These emails would contain a zip attachment that when opened would infect the computer. These zip files contain executables that are disguised as PDF files as they have a PDF icon and are typically named something like FORM_101513.exe or FORM_101513.pdf.exe. Since Microsoft does not show extensions by default, they look like normal PDF files and people open them.
Please make sure that your antivirus/malware software and systems are up to date. And for Pete’s sake do NOT open attachments from the likes of those listed. IF you think you need to track something go to the ‘front door’ of the shipping company or bank and login/track there.
Once YOU infect yourself (yes, it is an action taken by the user that starts the infection!!) [Like any other piece of malware, common sense goes a long way. The critical thing is it’s not going to install files by itself. You have to initiate some action.] you will soon probably see a screen that looks like this:
Examples of known CryptoLocker email subjects include:
|
USPS – Your package is available for pickup ( Parcel 173145820507 ) |
USPS – Missed package delivery ("USPS Express Services" <service-notification@usps.com>) |
|
USPS – Missed package delivery |
FW: Invoice <random number> |
|
ADP payroll: Account Charge Alert |
ACH Notification ("ADP Payroll" <*@adp.com>) |
|
ADP Reference #09903824430 |
Payroll Received by Intuit |
|
Important – attached form |
FW: Last Month Remit |
|
McAfee Always On Protection Reactivation |
Scanned Image from a Xerox WorkCentre |
|
Scan from a Xerox WorkCentre |
scanned from Xerox |
|
Annual Form – Authorization to Use Privately Owned Vehicle on State Business |
Fwd: IMG01041_6706015_m.zip |
|
My resume |
New Voicemail Message |
|
Voice Message from Unknown (675-685-3476) |
Voice Message from Unknown Caller (344-846-4458) |
|
Important – New Outlook Settings |
Scan Data |
|
FW: Payment Advice – Advice Ref:[GB293037313703] / ACH credits / Customer Ref:[pay run 14/11/13] |
Payment Advice – Advice Ref:[GB2198767] |
|
New contract agreement. |
Important Notice – Incoming Money Transfer |
|
Notice of underreported income |
Notice of unreported income – Last months reports |
|
Payment Overdue – Please respond |
FW: Check copy |
|
Payroll Invoice |
USBANK |
|
Corporate eFax message from "random phone #" – 8 pages (random phone # & number of pages) |
past due invoices |
|
FW: Case FH74D23GST58NQS |
Symantec Endpoint Protection: Important System Update – requires immediate action |
What should you do when you discover your computer is infected with CryptoLocker
When you discover that a computer is infected with CryptoLocker, the first thing you should do is disconnect it from your wireless or wired network. This will prevent it from further encrypting any files. Some people have reported that once the network connection is disconnected, it will display the CryptoLocker screen.
Users who are infected with the malware should IMMEDIATELY consult with a reputable security expert to assist in removing the malware. And should NOT attempt to mitigate or in anyway try to ‘fix’ the issue themselves – this will only insure the loss of data!!
It is not advised that you remove the infection from the %AppData% folder until you decide if you want to pay the ransom. If you do not need to pay the ransom, simply delete the Registry values and files and the program will not load anymore. You can then restore your data via other methods.
It is important to note that the CryptoLocker infection spawns two processes of itself. If you only terminate one process, the other process will automatically launch the second one again. Instead use a program like Process Explorer and right click on the first process and select Kill Tree. This will terminate both at the same time.
Is it possible to decrypt files encrypted by CryptoLocker?
Unfortunately at this time there is no way to retrieve the private key that can be used to decrypt your files without paying the ransom. Brute forcing the decryption key is not realistic due to the length of time required to break the key. Also any decryption tools that have been released by various companies will not work with this infection. The only method you have of restoring your files is from a backup or Shadow Volume Copies if you have System Restore enabled. Newer variants of CryptoLocker attempt to delete the Shadow Copies, but it is not always successful. There are methods that can/may be used to recovery you ‘Shadow Copies’, but this often times requires an expert.
If you do not have System Restore enabled on your computer or reliable backups, then you will need to pay the ransom in order to get your files back.
So to summarize the very first line of defense is to have good computing common sense and usage. Second if my usual mantra FULL IMAGE BACKUPS ON A REGULAR BASIS TO EXTERNAL/REMOVABLE MEDIA. I can’t say this enough. And I’m sure to get the calls from folks who are screwed. I sympathize, a little anyways.
Okay end rant. Be safe. Peace all.