Here I am going to show you how to install Windows 8 Consumer Preview into a Virtual Machine using VirtualBox. I will be showing the method for Check out my previous article on ‘Getting Started with Virtualization’ first for a good primer.Make sure you have plenty of free hard drive space – probably 30GB should be sufficient.
Make sure your processor supports virtualization AND 64bit processing.
To do that download ‘SecureAble’ from GRC.com and run it (after downloading it righ-click and choose ‘run as administrator’. Download is here.
You should see a screen like this screen
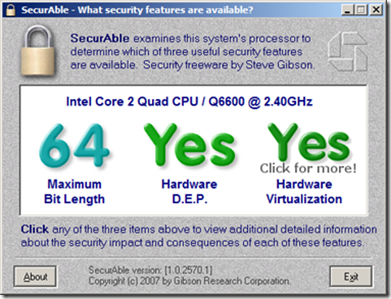
if your system will let you use Hardware Virtualization and has 64bit processing capabilities. IF it doesn’t there is NO need to continue. You will NOT be able to do anything mentioned here.
So let’s get started
Download the latest version of VirtualBox
Download Vbox Extensions Pack [To install you need to first install VirtualBox then double-click the extensions pack and it should be added to the VirtualBox installation]
Download Windows 8 Consumer Preview (64bit) (copy the Product Key to a text file too!)
Install all of these ‘as administrator’.
After installation:
1. Launch Virtual Box. (Make sure you’ve installed the Extensions pack) Click New to create a new virtual machine and type a name for it.
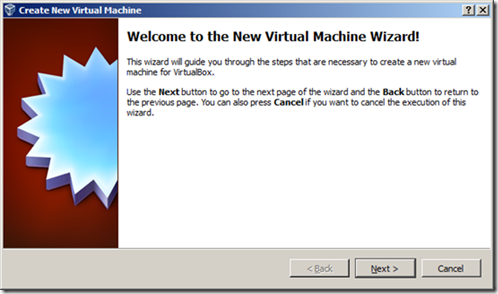
2. For Operating System version, select "Win8 64-bit"
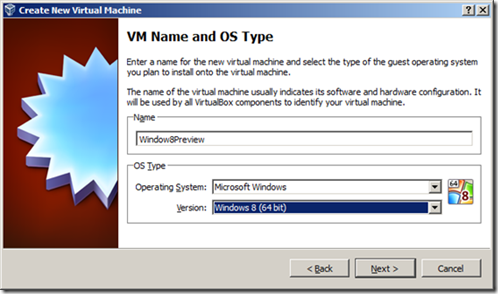
3. For memory size, enter 3090MB, more or less. Microsoft recommends 2GB at least for the 64-bit version. Click next/continue through the next screen to create a startup disk.
4. Click next/continue again to create a VDI file.
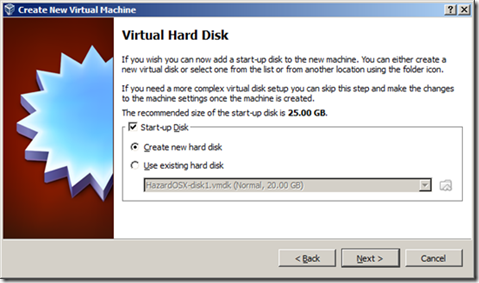
Then
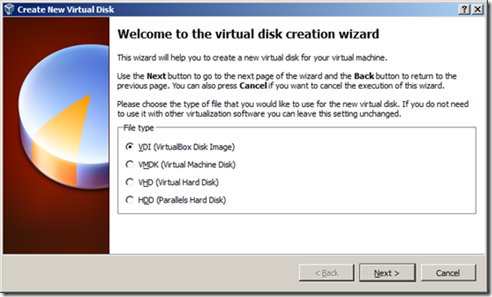
5. Use a Fixed size disk, for better performance (especially since this is just a test virtual machine).
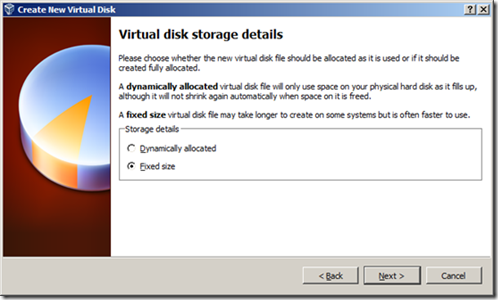
6. A 25GB disk size is probably fine; that’s the minimum Microsoft recommends for the 64-bit version.
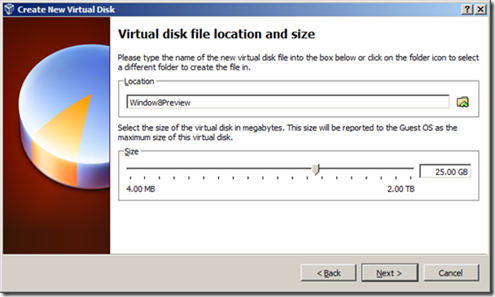
7. Click Create and your virtual disk file will be created.
And then..
Now you will have a new Virtual Machine – Windows8Preview, that we will need to make a few more edits to before we can start it.
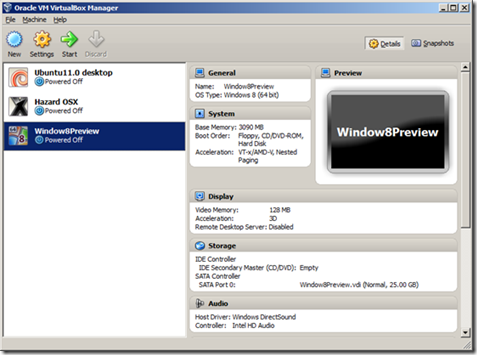
You’ll notice I have some other Virtual Machines here. [But we are only concerned with the Windows8Preview one for this article.]
So right-click on the Windows8Preview VM and click on ‘Settings’
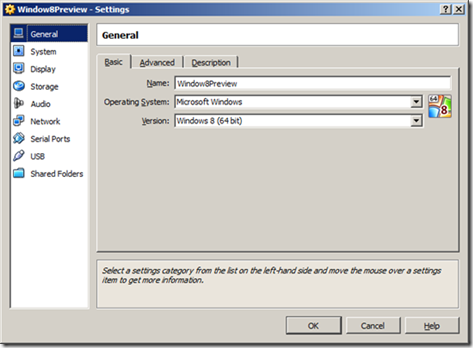
Under the ‘System’ options make sure to set the options to look like this:
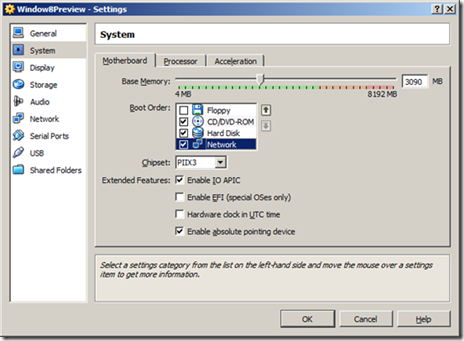
Click to the Processor tab and then check ‘Enable PAE/NX’
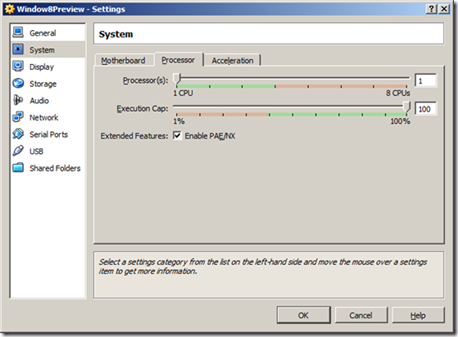
Under Acceleration: Enable VT-x/AMD-V and Enable Nested Paging
Next click on the Storage Options
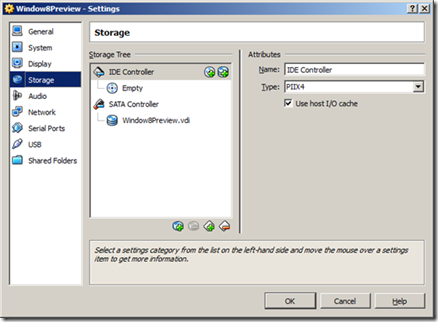
Click the CD icon next to CD/DVD Drive, then choose the virtual CD/DVD disk file to browse to the Windows 8 ISO file you downloaded.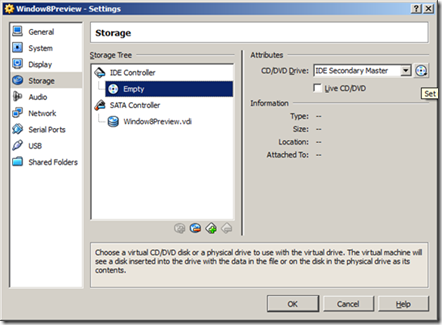
Then navigate to the directory where you downloaded the Windows 8 ISO file, click open.
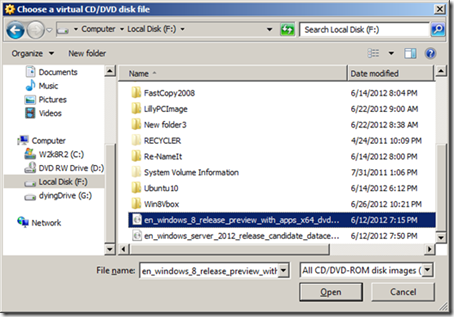
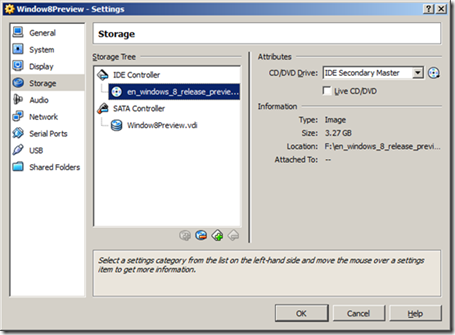
Finally click Start to begin the installation and walk through the Windows 8 installation.
TAKE NOTE THAT TO ‘REGAIN’ CONTROL OF YOU MOUSE OUTSIDE OF THE VIRTUAL MACHINE YOU’LL HAVE TO USE THE ‘RIGHT Ctrl’ TO FREE IT UP!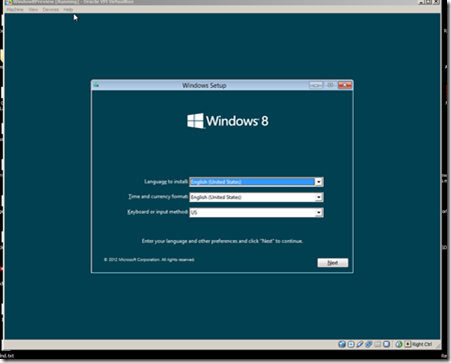
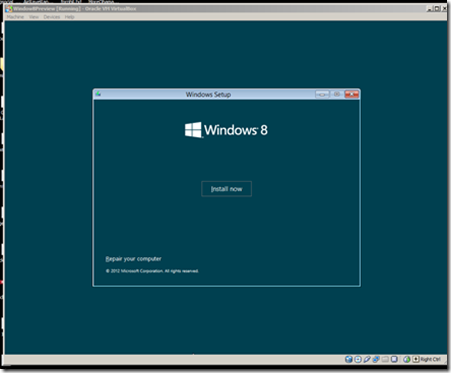
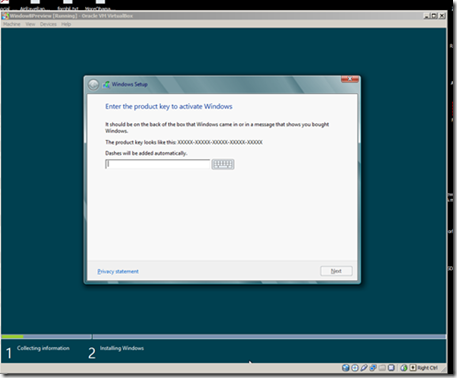
Press install and then you will have to enter the preview Key:
Choose Custom (New)install and then Next to select the drive (virtual Hard Drive we created)
The install will then start
Then walk through the setup:
Continue to walk through Setup, I chose to ‘Sign in without Microsoft account’ you can however if you wish use a hotmail or live mail account:
The important thing to know that with the mouse the ‘corners’ of the screen are where most stuff happens in the ‘Metro’ GUI. You can use your mouse to click and ‘scroll’ around the metro applications or move it over to a corner to pull up the ‘Charms’ on the lower right corner, recent applications on the upper right corner and the ‘faux start menu at the lower left.
The new Metro GUI will take a whole lot of getting used to.
It would be good to watch video first to get a little understanding of the system. (don’t fall asleep though ).
).
For me I doubt I will ever use Metro much except when I’m doing support for end users on their system. I have WAY too many applications for this type of interface and prefer the old Windows 7 Style Start Menu.
Thankfully that can easily be enabled in Windows 8. To do so – in Windows 8 Consumer Preview open Internet Explorer and go to this site, [here is the address so you can enter it manually if you need to http://www.stardock.com/products/start8/ ]
Enter an email address (hint – ANY will do) and download the application. Then once downloaded ‘right-click’ and choose ‘run as administrator’. And you will now have the old Start Menu and some new ‘right-click’ options such as ‘run’ shutdown’ and more.
Well, there is a start for you to mess around with Windows 8 and get a feel for the future of Windows Operating Systems. By using VirtualBox you don’t have to worry about messing up you current system. You can always delete your VM and start over or just get rid of it. 
I’m going to be adding a whole load more posts as time goes on on how to use Windows 8. This is such a big step for end users I foresee a whole lot of confused, frustrated and aggravated users.
Keep checking back for more.
![]()






























