Using PowerShell to Manage Windows Updates: PSWindowsUpdate
Often we have to update computers that have not – for whatever reason been updated in a long time. AND we often have to create new deploy images using sysprep. What usually happens is that Windows update will hang at ‘checking for updates’ for a very long time and either error out or never complete. A secret I found to deploying Windows Updates when this happens or from within Audit Mode is an excellent PowerShell module created by Michal Gajda. This module, aptly called PSWindowsUpdate, allows managing Windows Update on any computer running PowerShell 2.0 or higher. This module even enables Windows admins to check for and install updates on remote PCs and servers. PSWindowsUpdate is particularly handy for installing updates on Server Core machines that have no GUI, or in instances such as Sysprep’s Audit Mode where the Windows Update GUI doesn’t work.
· Get started by downloading the latest version of PSWindowsUpdate.zip.
· Once downloaded, extract the contents of the zip file to C:\Windows\System32\WindowsPowerShell\v1.0\Modules\.
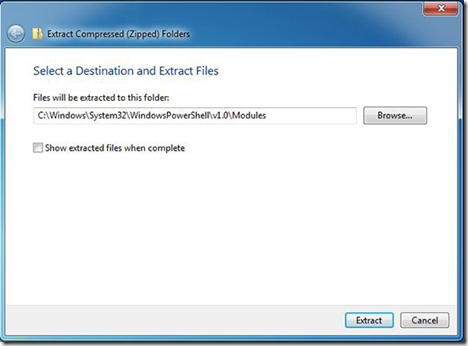
Extracting files from PSWindowsUpdate.zip.
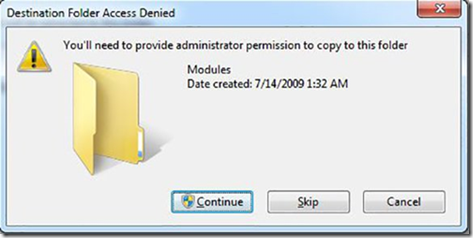
· Click Continue if a UAC prompt appears.
· When the files have been extracted into the PowerShell Modules folder, open an elevated PowerShell prompt. Change PowerShell’s Execution Policy to RemoteSigned. The RemoteSigned Execution Policy allows PowerShell scripts downloaded from the Internet to run on a PC as long as they are signed by a trusted publisher.
· Type Set-ExecutionPolicy RemoteSigned and press Enter. When prompted, confirm the change by pressing Y and then Enter.
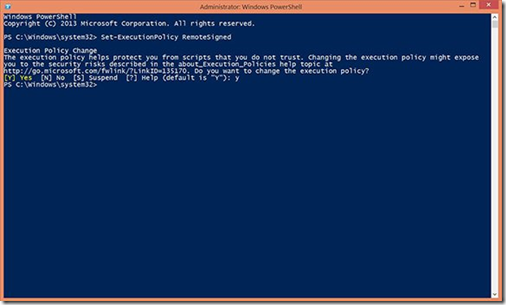
Changing PowerShell’s execution policy
This completes the one-time configuration of the module! Now it’s time to put PSWindowsUpdate to use!
· If running PowerShell v2.0, type Import-Module PSWindowsUpdate and hit Enter. This isn’t necessary in PowerShell v3 and higher, but it doesn’t hurt anything either. This step simply guarantees that the modules cmdlets will be available to the PowerShell v2.0 session.
· Display a list of all the module’s available cmdlets by typing Get-Command –module PSWindowsUpdate and hitting Enter.
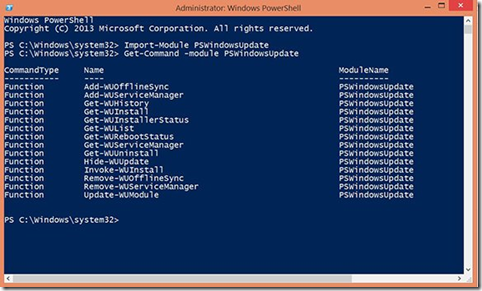
Using Get-Command -module PSWindowsUpdate.
· Possibly the most important function for getting and installing updates is Get-WUInstall. Help for each cmdlet is available, so to see full help for Get-WUInstall type Help Get-WUInstall –full and press Enter.
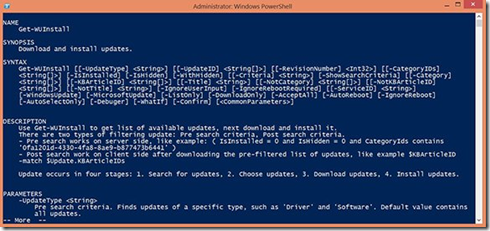
Looking at help for Get-WUInstall.
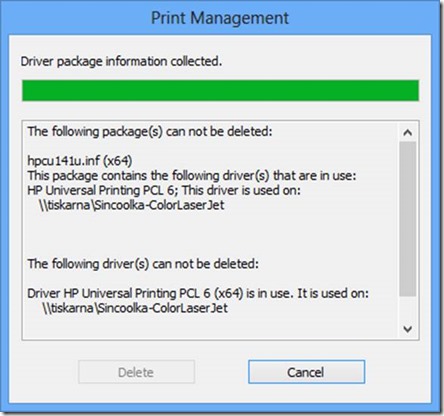
When applying updates, I prefer connecting to the Microsoft Update servers. Using these instead of the standard Windows Update servers allows installing updates to Office and other Microsoft products in addition to the normal Windows updates. Unfortunately, trying to connect to the Microsoft Update servers using the PSWindowsUpdate module from a fresh Windows installation will produce an error, as shown below.
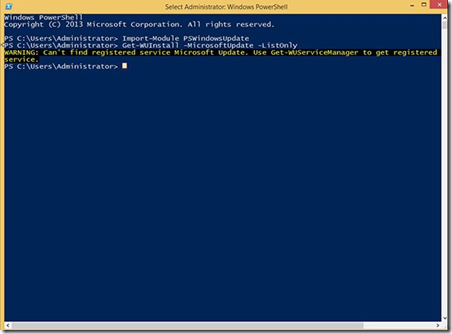
· The reason for this error is because Windows is registered to use only the standard Windows Update servers by default. To use the Microsoft Update servers, the Microsoft Update Service must be registered on the computer. In the GUI, this is done by selecting the checkbox for Give me updates for other Microsoft products when I update Windows from the Control Panel – Windows Update – Change Settings applet.
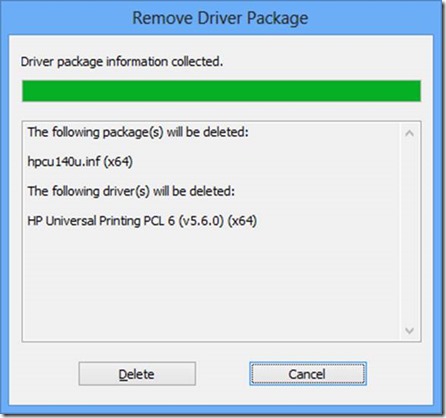
· In the PSWindowsUpdate module, the same process is completed by using the Add-WUServiceManager cmdlet with the ServiceID for the Microsoft Update service specified. Type Add-WUServiceManager -ServiceID 7971f918-a847-4430-9279-4a52d1efe18d and press Enter. When prompted, confirm registering the service by typing Y and pressing Enter one more time.
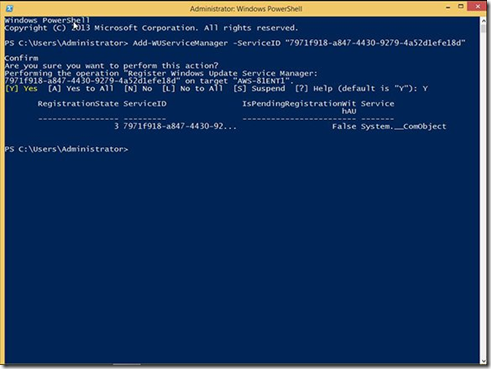
Registering the Microsoft Update servers.
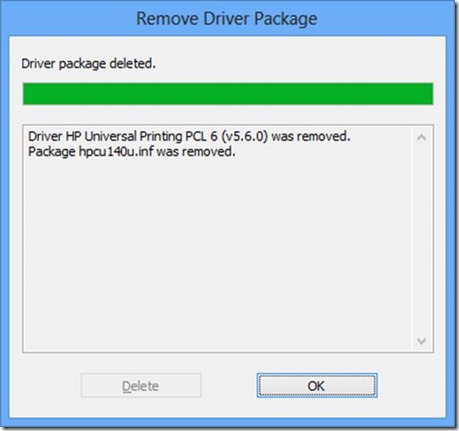
· List available updates from the Microsoft Update servers by typing Get-WUInstall –MicrosoftUpdate –ListOnly and pressing Enter. After a few moments, the system will return a list of the available updates for the current machine. No error this time!
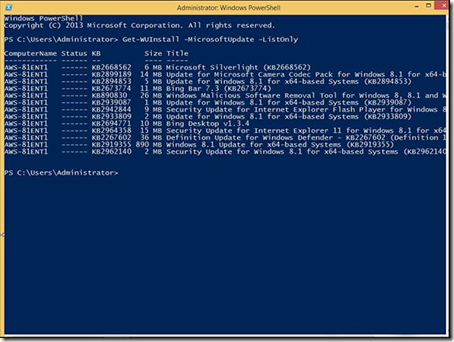
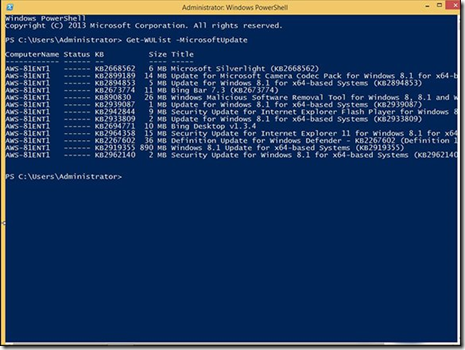
· The same results are produced by typing Get-WUList –MicrosoftUpdate and pressing Enter.
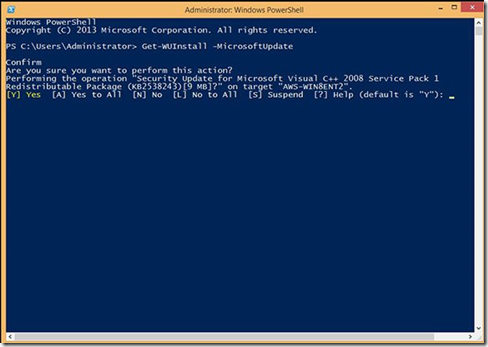
· Type Get-WUInstall –MicrosoftUpdate and press Enter to go through the available updates, confirming installation of each one manually.
PSWindowsUpdate and Parameter Support
Another awesome feature of the PSWindowsUpdate module is its support of parameters. For example, using the –AcceptAlland the –AutoReboot parameters with the Get-WUInstall cmdlet changes the manual process into an automated one. Type Get-WUInstall –MicrosoftUpdate –AcceptAll –AutoReboot and press Enter. The system will download and install all available updates and then automatically reboot if any of the updates require a reboot.
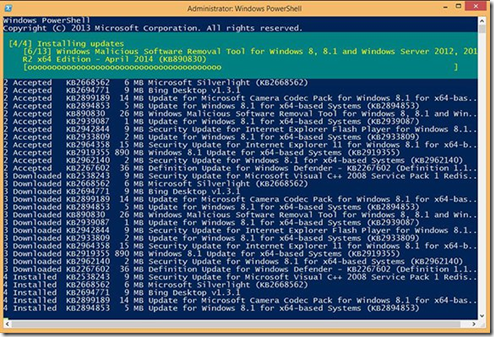
Retrieving updates and installing automatically.
Don’t want a particular update to be installed? No problem! Use Hide-WUUpdate. Selection parameters such as –Title or –KBArticleID narrow in and hide specific updates. Feel free to use wildcards with these parameters. As an example, type Hide-WUUpdate –Title “Bing*” –KBArticleID “KB2673774” –MicrosoftUpdate –Confirm:$false and press Enter to hide the Bing Bar 7.3 update.
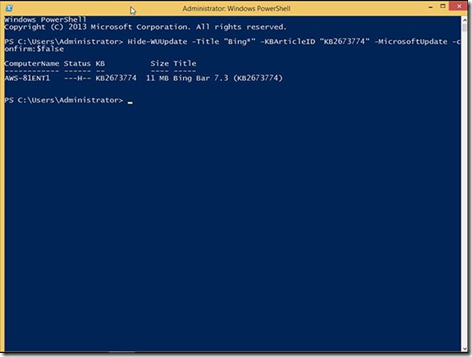
Hiding an unwanted update.
Notice that I used the –Confirm parameter, along with the $false switch, to automatically confirm hiding the selected update. In the future the update won’t appear when listing available updates.
Did you make a mistake and hide the wrong update? No problem! Hide-WUUpdate can unhide an update by using the –HideStatus parameter with the $false switch. To unhide the update hidden earlier, type Hide-WUUpdate –Title “Bing*” –KBArticleID “KB2673774” –MicrosoftUpdate –HideStatus:$false –Confirm:$false then press Enter. As before, I used the –Confirm:$false parameter to keep everything streamlined.
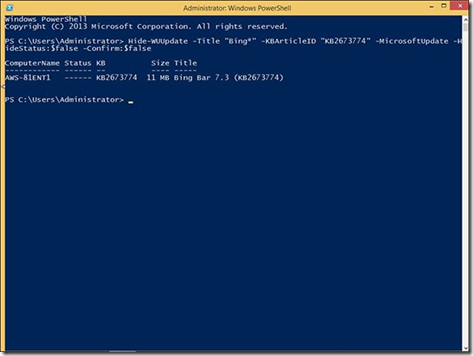
Unhiding a previously hidden update.
Once all the updates are complete make sure to open PowerShell (as Administrator) and set the Execution Policy back to ‘restricted’:
Type Set-ExecutionPolicy Restricted and press Enter. Then exit